Ubiquitous and inconspicuous, connected devices have become such an integral part of life that we barely register them. But the infamous stories of hacking raise an important question: Are IoT devices secure? How do we protect them from exploitation by malicious parties wanting to steal our data or cause physical harm?
That’s where regulators step in, promoting policies and frameworks that set standards for IoT security. In the next sections, we examine the most recent changes to the regulatory landscape and how IoT device vendors and users can comply with them.
1. Securing IoT Devices: A Brief History of IoT Regulation
The first attempts to standardize the IoT field and ensure device security were made after the technology had already achieved widespread use. In 2014, the US National Institute of Standards and Technology (NIST) published a digital security policy for private companies. Although this policy didn’t focus specifically on IoT device security, its guiding principles applied to IoT, and it was praised worldwide as a regulatory success.
In 2015, the Internet of Things Global Standards Initiative (IoT-GSI) convened in Geneva. Its goal was to “promote a unified approach [...] for development of technical standards (Recommendations) enabling the Internet of Things on a global scale.” Because the initiative was led by a non-governmental organization, namely the International Telecommunications Union – Telecommunications Standardization Sector (ITU-T), the proposed standards had only an advisory nature.
The first notable piece of legislation regulating IoT device security specifically, was the US IoT Cybersecurity Improvement Act of 2020. This law established NIST and the Office of Management and Budget (OMB) as the parties responsible for developing and updating IoT security standards for government agencies. The regulation essentially prohibited agencies from purchasing and using IoT devices unless they were compliant with minimal security standards developed by the NIST and OMB.
In the EU, a similar landmark document was the EU Cybersecurity Act, enacted in 2019. In 2020, it was complemented by the European Telecommunications Standards Institute (ETSI) EN 303 645 standard, which we’ll discuss in more detail below.
2. Most Recent Сompliance Regulations on IoT Device Security
Between 2020 and 2022, the EU and governments worldwide enacted a number of important regulations for the IoT field. Entities that operate in the EU and meet specific criteria fall under the scope of Directive (EU) 2022/2555; consumer IoT devices are covered by EN 303 645; and industrial IoT systems are regulated by ISA/IEC 62443. Let’s take a look at these impactful regulations and standards.
2.1 Network and Information Security Directive (NIS)
The Network and Information Security 2 (NIS 2) Directive, also referred to as Directive (EU) 2022/2555, aims to enhance cybersecurity across the European Union by holding it up to a uniformly high standard. NIS 2 requires EU member states to ensure that relevant entities, which are basically all providers and users of digital products, take appropriate technological, operational, and organizational measures to manage cybersecurity risks.
NIS 2 has a years-long implementation timeline:
- Member states have 21 months, until 17 October 2024, to transpose its measures into national law and apply them by October 18, 2024.
- By January 17, 2025, the Cooperation Group should establish a methodology and organizational aspects of voluntary peer review to share experiences and improve security across member states.
- By April 17, 2025, each member state should create a list of “essential and important entities” that fall under the scope of this directive” and entities providing domain name registration services.”
- By October 17, 2027, and periodically every three years, the European Commission will review and report to the European Parliament and Council how well the directive works.
According to the directive, member states should implement the following to ensure cybersecurity, including IoT device security:
- Risk analysis and information system security policies
- Incident handling
- Backup management and disaster recovery
- Supply chain security
- Security in network and information systems acquisition, development, and maintenance
- Cybersecurity training
- Multi-factor authentication or continuous authentication solutions, where appropriate
Entities that should comply with NIS 2, as listed in Article 26 of the directive, include:
- Domain Name System (DNS) service providers
- Domain name registration service providers
- Cloud computing service providers
- Data centers
- Online search engines
- Social networking services platforms
- Content delivery network providers
- Security service providers
- Managed service providers
- Online marketplaces
An entity established outside the EU that offers its services in the EU must designate a representative responsible for compliance with NIS 2 who is located in a member state. If a representative is not established, the member state can take legal action against the entity for violating the directive.
2.2 European Telecommunications Standards (ETSI)
The standard adopted by the European Telecommunications Standards Institute (ETSI), EN 303 645, establishes a security baseline for all consumer IoT devices. Released in June 2020, it resulted from collaboration between industry, academics, and government.
The goal of ETSI EN 303 645 is securing IoT devices against large-scale attacks. This standard covers devices such as:
- Connected baby monitors and children’s toys
- Connected smoke detectors, window sensors, and door locks
- Smart cameras, speakers, and TVs
- Wearable health monitors and trackers
- Connected home automation and alarm systems
- Connected appliances (e.g., refrigerators and washing machines)
- Smart home assistants
- IoT gateways, stations, and hubs that connect to multiple devices
Healthcare IoT devices used in hospitals and connected devices used for manufacturing or commercial purposes are not regulated by ETSI EN 303 645.
ETSI EN 303 645 has thirteen principles:
- No universal default passwords
- Devices should automatically report vulnerabilities
- Software updates should be automated, timely, and secure
- Secure storage of sensitive parameters
- Secure communication
- Minimization of exposed surfaces
- Software integrity should be ensured
- Secure all personal data
- Resilience to outages
- Examination of system telemetry data for security anomalies
- Users can easily delete their own data
- Easy device installation and maintenance
- IoT devices should validate all data that is input through user interfaces, Application Programming Interfaces (APIs), or networks
Although originally developed for the EU Cybersecurity Act to provide a more specific definition of IoT device security, ETSI EN 303 645 has been widely adopted outside the EU. While nonbinding in and of itself, this standard became the foundation for national IoT certification systems for many countries, including the UK, Germany, Finland, Singapore, India, Australia, and Vietnam.
Sharing ETSI EN 303 645 as the basis of their national policies allows countries to honor each other’s IoT certification systems. For example, Singapore’s certificates are recognized in Finland and Germany, and vice versa.
2.3 ISA/IEC 62443 Standards
Since 2010, the International Society of Automation (ISA) 62443 standards have provided detailed requirements for the security of industrial automation systems. However, in 2021, the International Electrotechnical Commission (IEC) recognized ISA 62443 as “horizontal standards.” That means those cybersecurity policies are applicable across a broad range of sectors.
ISA/IEC 62443 standards cover the security of IoT devices and other automation elements in such industries as:
- Manufacturing
- Metals and mining
- Power utilities
- Water management
- Healthcare
- Transportation
Additionally, these standards provide guidance on:
- Defining cybersecurity terms and concepts for use by all stakeholders
- Determining a reasonable level of security for each business entity
- Establishing cybersecurity methodology for product developers
- Defining risk assessment processes that are critical to system security
Unlike NIS 2 and ETSI EN 303 645, which were developed in the EU, ISA/IEC 62443 is an example of a truly global standard. Ninety countries are either full or associate members of the IEC, aligning their domestic cybersecurity policies with its standards. Some notable member states are:
- Australia
- Brazil
- Canada
- China
- France
- Germany
- India
- Japan
- Mexico
- UK
- US
For any manufacturing company interested in entering these markets or a vendor working with such companies, ISA/IEC 62443 compliance becomes critical.
3. Who Needs To Comply With The New Standards?
NIS 2 and ETSI EN 303 645 technically have legal power only within the EU. Some markets and industries enforce ISA/IEC 62443 standards more rigorously than others. However, many companies choose to comply with both sets of standards voluntarily, even when they aren’t legally required to. Let’s take a closer look at industries where compliance is either required or makes particular sense.
3.1 Healthcare
If medical IoT devices experience a cyberattack that causes health damage, healthcare institutions can face extreme liabilities. In a realistic cyberattack scenario simulated by Meddevice Online, the target was a connected device implanted in 10,000 patients.
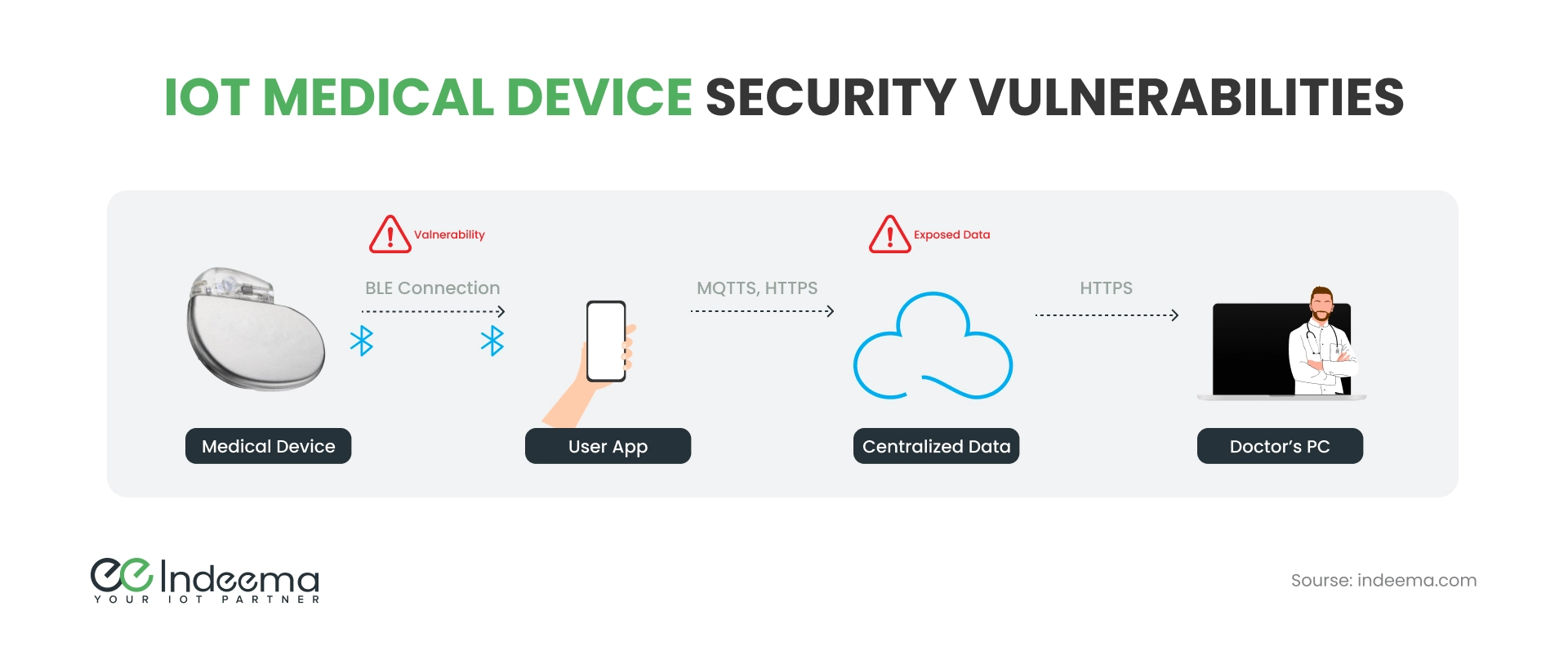
In the simulation, when ransomware infected the devices, the healthcare providers issued an alert asking patients to delete the app they used to monitor their devices. However, only half of the simulated patients complied with the request within 48 hours. After that, the hackers successfully used a malicious app update to “brick” the remaining 5,000 devices.
The simulated company was faced with paying for 5,000 surgeries to remove the now-useless implants, costing a total of $250 million, and the ensuing lawsuit cost another $700 million. In real life, no company would possibly be able to recover after such astronomic damages and the crushing blow to its reputation. This simulated case highlights the pivotal importance of medical device IoT security.
3.2 Transportation
Similarly to healthcare providers, transport companies can face extreme litigation costs if their vehicle software is hijacked and used to harm people. In the infamous 2015 SUV hack, attackers gained remote control over a vehicle, making it speed up and then veer off the road. That incident made vehicle manufacturers take cybersecurity seriously, but vulnerabilities allowing control over car functions are still discovered, even in top models.
While transport providers have no direct control over automotive IoT device security vulnerabilities, they need to be aware of best security practices so they can choose safe models for their fleets and pressure automobile manufacturers to increase security.
3.3 Consumer electronics
With attacks on connected devices making headlines, people are becoming more concerned about their devices' security. PSA Certified found that 65% of consumers look for security information when buying electronics for personal use. What’s more, 69% of respondents happily paid a premium for a safer device.
Customer preferences like these give an edge to consumer electronics manufacturers that invest in security. Conversely, companies that lack security protections might lose out on significant sales.
3.4 Anyone who stores sensitive data
This category includes banks and financial companies, but it isn’t limited to them. Basically, every company that stores and processes customers’ personal or payment data, including payment systems, online marketplaces, cloud service providers, and iGaming operators, falls into this category.
Every IoT device these companies operate, even a supposedly harmless one, brings increased risk. For example, a casino was hacked through the connected thermostat in its lobby aquarium. Cybercriminals penetrated the company’s entire network and stole the database of high-roller players, including their personal and payment data. Such incidents highlight the need to secure all IoT devices — one vulnerable device can expose the entire network it’s connected to.
3.5 B2B vendors
NIS 2 and ISA/IEC 62443 contain requirements for supply chain security. For this reason, companies demand that their vendors comply as well. Amazon Web Services (AWS), for instance, requires ISA/IEC 62443 compliance from its partners. As a B2B product or service provider partnering with AWS, you can lose customers if you don’t meet AWS IoT security expectations.
As you can see, virtually every company in today’s market must secure its IoT devices, be it because of regulatory requirements, market pressures, or the tremendous damage a successful attack can cause. However, many businesses, especially smaller ones, aren’t sure how to secure IoT devices, and many are leery of the cost.
4. How to Achieve Secure Connectivity Across All Routes
What if you could keep all your IoT data encrypted end-to-end so that even if a malicious party manages to intercept it, they’d only get a useless string of bytes?

Microchip Connectivity Framework (MCF) does exactly that. Indeema Software partnered with Microchip Technology Inc. to deliver MCF — a set of software libraries and tools that enable a fully encrypted universal messaging system. All information exchange between nodes occurs on a secure MCF network, and only the intended recipient can read encrypted messages. Neither the local server vendor nor the cloud service provider has access to message content.
Implementing MCF into device communication can help your company achieve compliance with:
- The hardware and cloud guidelines of NIS 2 and ETSI EN 303 645
- The sensitive data encryption and system integrity guidelines of ISA/IEC 62443
These standards and directives require company-wide policies and extensive staff training, so a stand-alone MCF investment can’t ensure 100% compliance with regulations. However, with the MCF technology, you can rest assured that data sent to and received by your IoT devices remains secured.
5. Keep Your IoT Network Safe With MCF
We interact with Internet-of-Things (IoT) technology far more often than we realize. IoT surveillance cameras and radars monitor roads for speeding. Some of us even live in smart homes. Hospital staff use medical IoT devices to support and monitor their patients.
Responding to concerns about safety, new regulations reflect IoT device security best practices. The newest regulations are NIS 2, ETSI EN 303 645, and ISA/IEC 62443. Industries such as healthcare, where a hacked IoT device risks tremendous liability, are increasingly adopting these standards.
Microchip Connectivity Framework encrypts all data your IoT devices send and receive to achieve partial compliance with NIS 2, ETSI EN 303 645, and ISA/IEC 62443. Indeema is the only Microchip-authorized partner that helps companies create, configure, and support the cloud or on-premises infrastructure needed for the MCF network.
