People love how their IoT devices stay connected 24/7, update information automatically, and require minimal user intervention—if any at all. However, this convenience may come at a price. Knowing the weak spots in IoT messaging security, hackers can access devices, steal data in transit, or use these devices as part of a botnet to launch massive attacks (as in the infamous Mirai assault).
Does that mean we must choose between security and convenience? Certainly not. By properly securing IoT networks with up-to-date methods, people can enjoy both. In this article, we’ll examine some emerging secure messaging protocols and frameworks, their strengths and weaknesses.
1. Secure IoT messaging is critical
IoT devices are more than smartwatches counting your steps and cameras for watching your pets when you’re away—IoT networks are often used to transmit sensitive information. Think hospital networks and wearable devices transferring patients’ health data or banking apps sending data about financial transactions from millions of smartphones. By hacking into a network like this, hackers can get their hands on large volumes of confidential data and use it for fraud, identity theft, or blackmail.
Besides, IoT devices are seldom used on a stand-alone basis. Typically, they’re connected into networks, and a single device falling under attack endangers the whole network. In one case, a casino was even penetrated through a thermostat in the lobby aquarium.
As these risks became apparent, it led to encryption being widely adopted to protect data in IoT messaging. So even if encrypted data gets compromised, the malicious actor is left with a useless sequence of bytes they can’t decipher without a key.
Another common technique is ongoing authentication, where a smart device has to complete an identity check for every interaction with the network. However, this method is energy-consuming and involves a tradeoff between sustainability and bandwidth constraints. To resolve this problem, lightweight messaging protocols such as Message Queuing Telemetry Transport (MQTT) came into use. While being secure, MQTT and the like minimize the code footprint and performance slowdowns in IoT systems.
Overall, lightweight messaging protocols are considered a great fit for IoT security frameworks. However, they’re still far from ubiquitous.
2. What are some up-to-date ways to ensure IoT messaging security?
As cyberattacks become more sophisticated, methods of securing IoT networks are evolving to meet the challenge. Let’s look at several recent framework solutions designed for various types of IoT networks, including healthcare, cloud services, and smart homes.
2.1 A Framework to Protect Medical Information
Proposed in 2019, this IoT security framework aims to protect medical information while using as few resources as possible. It generates unique pairs of keys from a patient’s electrocardiogram (ECG) data using the direct sequence spread spectrum (DSSS) method as shown below.
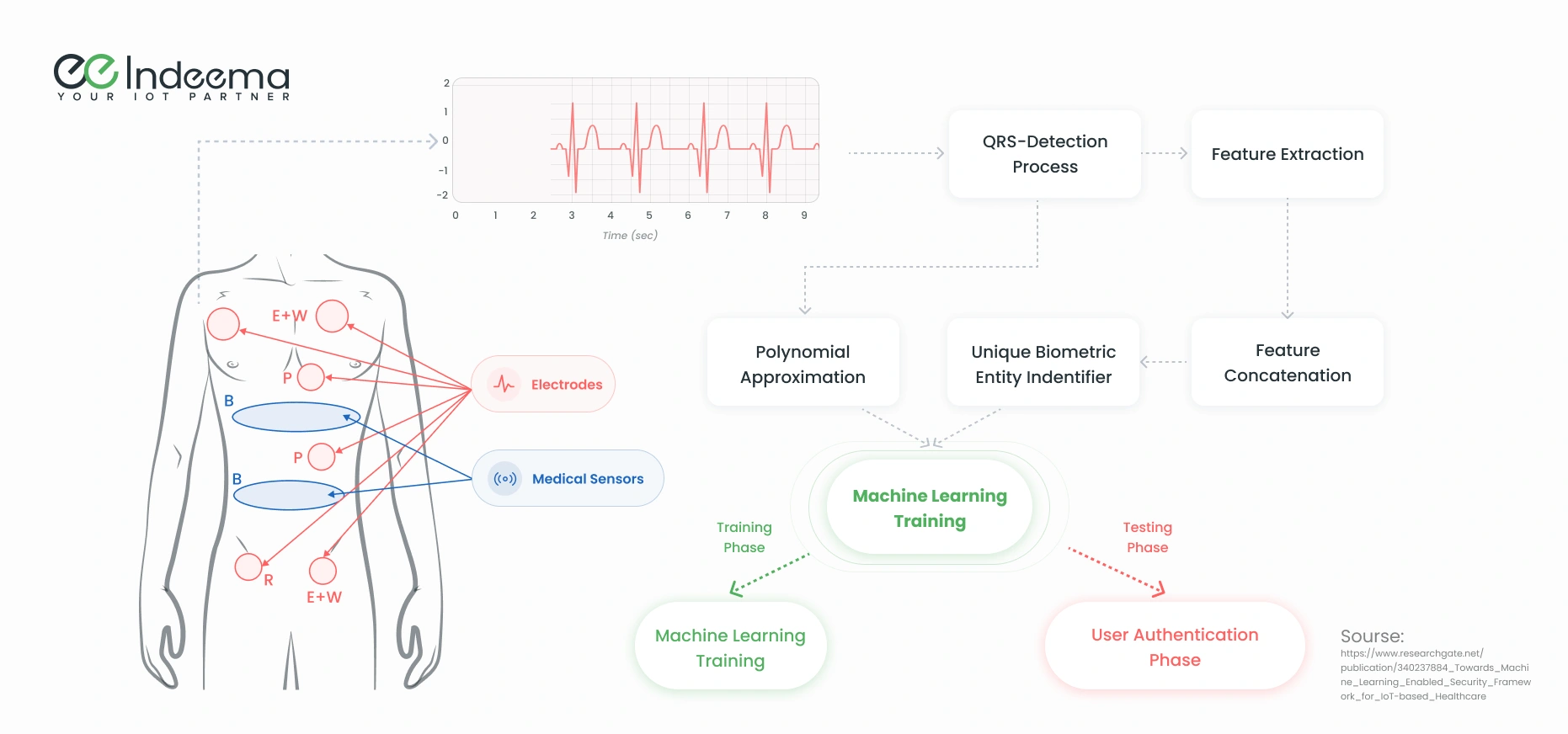
The key generation and authentication process follows these stages:
- The raw ECG signal gets DSSS-encrypted.
- From the patient’s ECG data, the QRS complex is calculated.
- The QRS complex undergoes non-linear transformation to create a random and unique key.
- This key, created from the patient’s biometric data, is used for authentication.
- If the user requesting the data fails the authentication check, they get disconnected. If the user passes the check, they get access to the data.
This framework adheres to the principles of healthcare data security:
- Data integrity and privacy: The data is encrypted in transit. Even if malicious actors steal it, they won’t be able to decipher it without a key.
- Data freshness: The data is updated and encrypted in real-time.
- Data availability: The data is easily available to authorized users and only to them.
- Secure key distribution: Each key is unique as it is generated from the patient’s ECG data.
The proposed framework solves the problems of efficient communication and resource effectiveness in securing medical IoT networks. However, this model relies on ECG data obtained through wearable sensors as its cornerstone. It’s unclear how it can be adapted for IoT systems that do not typically collect ECG data.
2.2 A Lightweight IoT-based Security Framework for Inventory Automation
This framework was developed to augment existing inventory automation security solutions, such as SIMON or SPECK, which remain vulnerable to particular types of attacks. The proposed security approach follows three steps:
- Registration: Every device joining the network gets registered with the inventory server (IS). In this process, the IS generates a unique set of keys for the device that are subsequently used for authentication. The shared key is computed by the IS from a nonce value.
- Lightweight authentication: At the start of each interaction, the device and the IS authenticate each other using secret keys and a hash function. Communication proceeds only if authentication is successful.
- Encryption: All data exchanged between the device and the IS is encrypted using the XOR method. The shared key of 128 bits is divided into two halves (64 bits each). In the first half, the number of 1s in each byte is calculated. The second half is used to XOR every data block of 64 bits. Finally, every byte of the XOR-ed plaintext is permutated. The permutated text and the sequence of numbers obtained from the first half of the shared key are crossed over to generate the final cipher text.
This framework is unique in that it combines a lightweight (less energy-consuming) approach and built-in authentication. When compared with SIMON and SPECK, the proposed framework demonstrated a 10% stronger security impact (measured as a combination of block size, key size, and round number) while needing 10% less time to execute and using 4% less memory. This superior performance makes it desirable to adopt for securing inventory management IoT networks. While this framework can potentially be adopted for other types of IoT networks, such as healthcare IoT or smart home environments, its efficiency in these scenarios is unknown as yet.
2.3 The Secure and Compliant Continuous Assessment Framework for Cloud Services
This framework, abbreviated as SCCAF, was proposed to evaluate security and compliance levels in cloud services. SCCAF includes the processes of security assessment, compliance assessment, and taking measures, as shown below.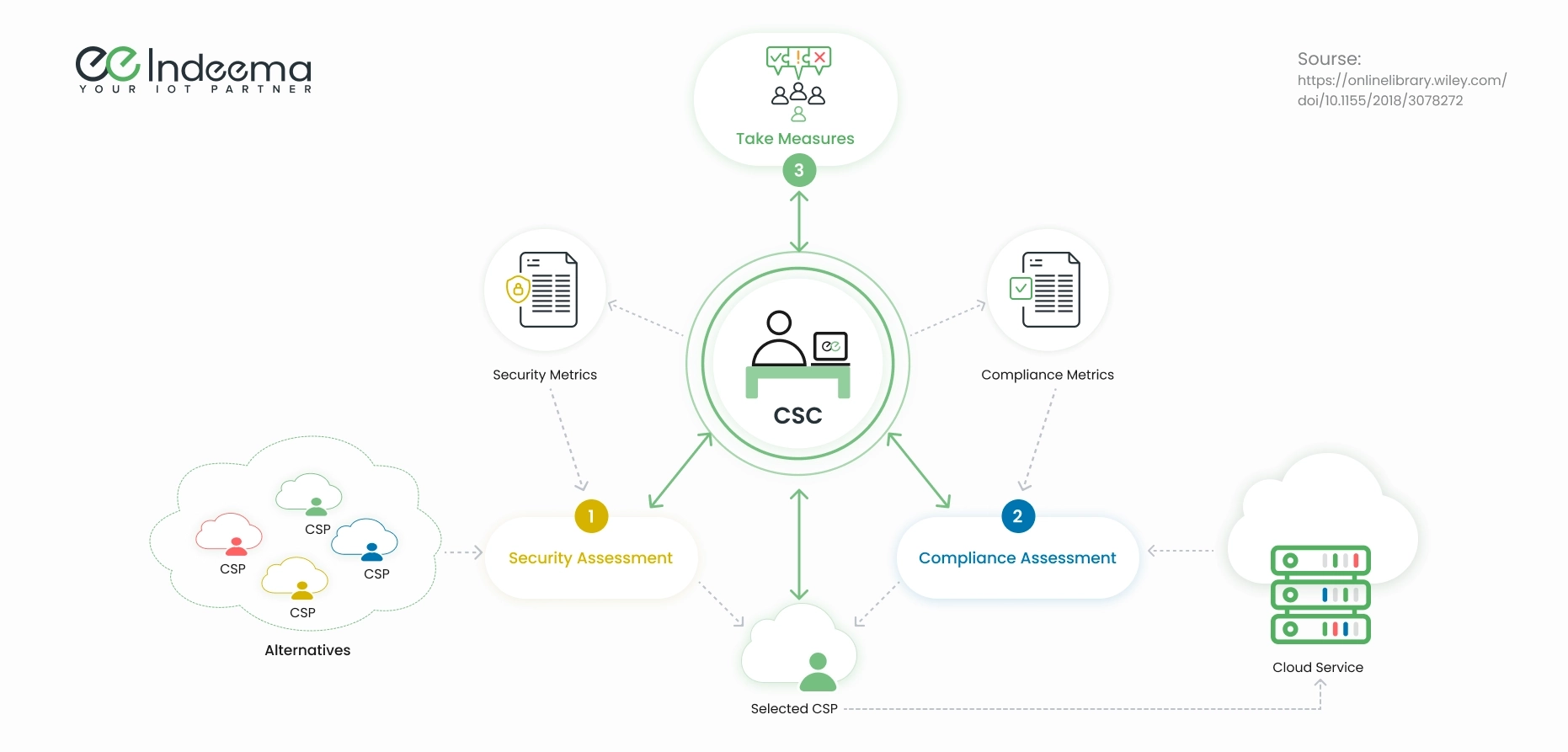
SCCAF is implemented as follows:
- Security assessment: The cloud services customer (CSC) evaluates the security levels of cloud service providers (CSPs) they’re considering. To do this, the customer compares the security provisions reported by the provider against the security metrics defined by the customer. As a result, the customer selects the optimal cloud service for their business needs and the required level of IoT security.
- Compliance assessment: While using their chosen CSP, the customer evaluates the compliance between the reported security measures and the actual state of security. In this process, the customer focuses on the metrics that matter most to them.
- Take measure: After completing both assessments, the customer makes a decision to continue using this service or to look for another provider.
This framework defines a set of security and compliance metrics that customers can use to evaluate CSPs. However, it doesn’t prescribe any particular course of action to take except the generic three steps outlined above. While this makes SCCAF extremely versatile, it also requires users to invest a significant amount of time and effort to work out the set of metrics that suits their business needs. Similarly, SCCAF provides no specific guidelines to CSPs who wish to improve their security.
2.4 The Enhanced Security Framework for Smart Devices
In 2017, an enhanced security framework for IoT devices in a smart home environment was proposed. Its architecture is shown below.
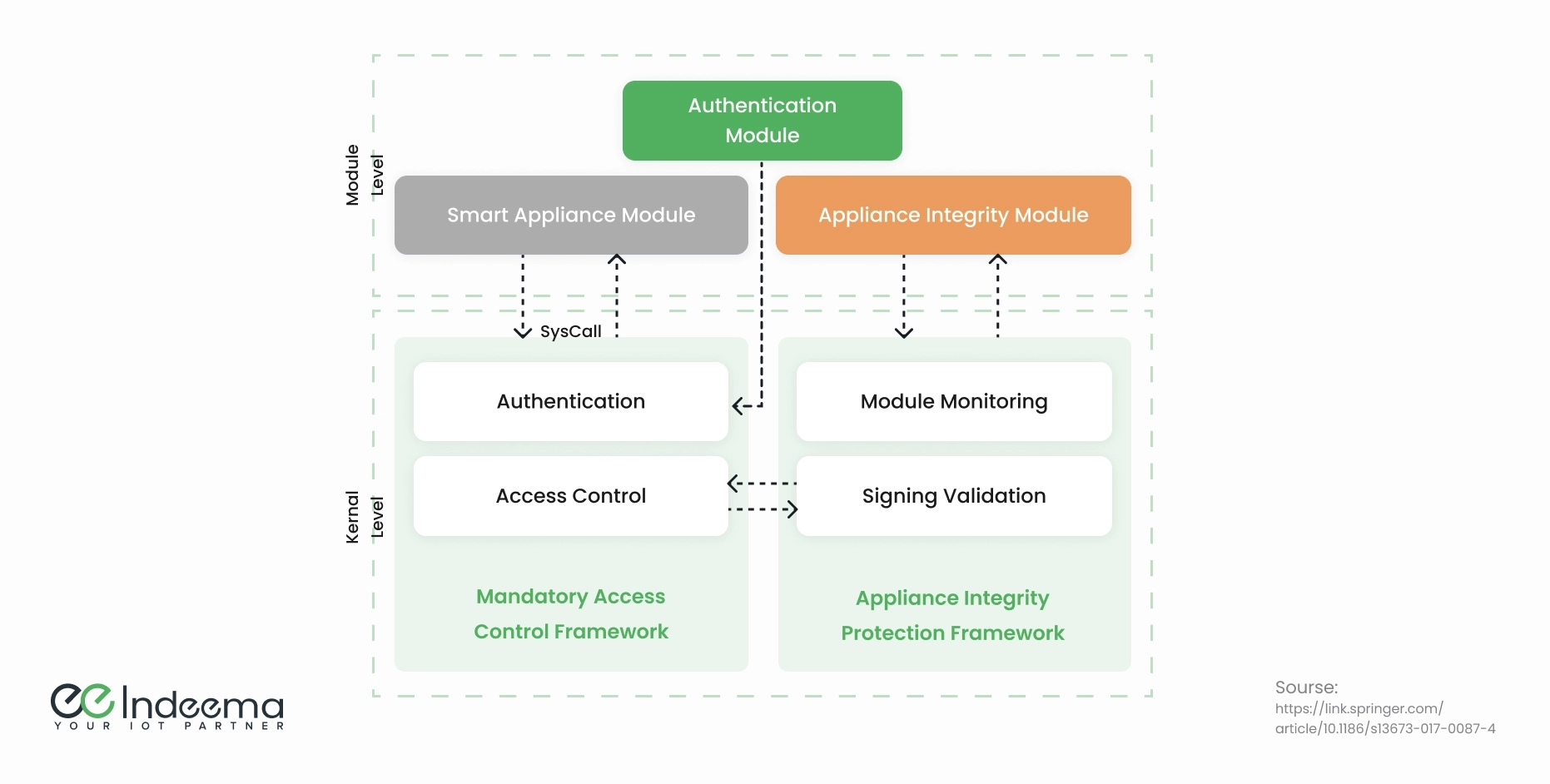
This framework is made up of:
- Smart appliance module: A basic level of security, the smart appliance is the actual IoT device, one of the many comprising the smart home network.
- Appliance integrity module: This is a more advanced level of security, a built-in module that monitors all smart devices in the network, checking their manufacturer’s signature. A device without such a signature is denied access.
- Mandatory access control framework: This framework controls each smart appliance’s rights and role, terminating operations that are irrelevant to their role: for example, if a washing machine requests access to surveillance cameras.
- Appliance integrity protection framework: This framework double-checks the manufacturer’s signature for each smart device.
The proposed framework adheres to the three principles of smart home security:
- Integrity: The codes of each device are checked through self-signing. All modules are constantly monitored for suspicious (role-irrelevant) activities. If such activity is detected, the module is forcibly restarted or disconnected from the network.
- Availability: The proposed framework improves availability by using a module role list for security checks. This simplifies the vector space used for encryption and minimizes performance disruptions and slowdowns. However, this system is still vulnerable to a malignant module lowering availability. If a hacked device is deliberately slowed down, such activity won’t be identified as suspicious as it doesn’t involve a role violation.
- Authentication: The authentication process in this framework is applied continuously to existing and newly added modules alike. Any module that fails authentication gets disconnected.
This smart home security framework introduces several notable improvements over earlier models. One such improvement is ongoing integrity and authentication monitoring. In earlier models, an integrity check was only performed when connecting a new device, which meant if an already trusted device was hacked, it endangered the entire network.
Another improvement is using a role list to minimize computation and performance slowdowns. However, this framework isn’t lightweight and remains vulnerable to attacks that specifically target device and/or network availability.
None of the frameworks we discussed are applicable to just any type of IoT network. The Enhanced Security Framework is focused on smart homes, the Lightweight IoT-based Approach on inventory automation, and the Framework to Protect Medical Information on healthcare data. The more versatile SCCAF lacks specificity, such as prescribing an encryption method.
3. But… is there a better security framework?
Yes, and it’s the first of its kind. Microchip Connectivity Framework (MCF) provides an application-layer stack for universal secure IoT connectivity. Developed by Microchip and implemented by Indeema Software, this framework adds an application layer to the existing security system, augmenting it as shown below.
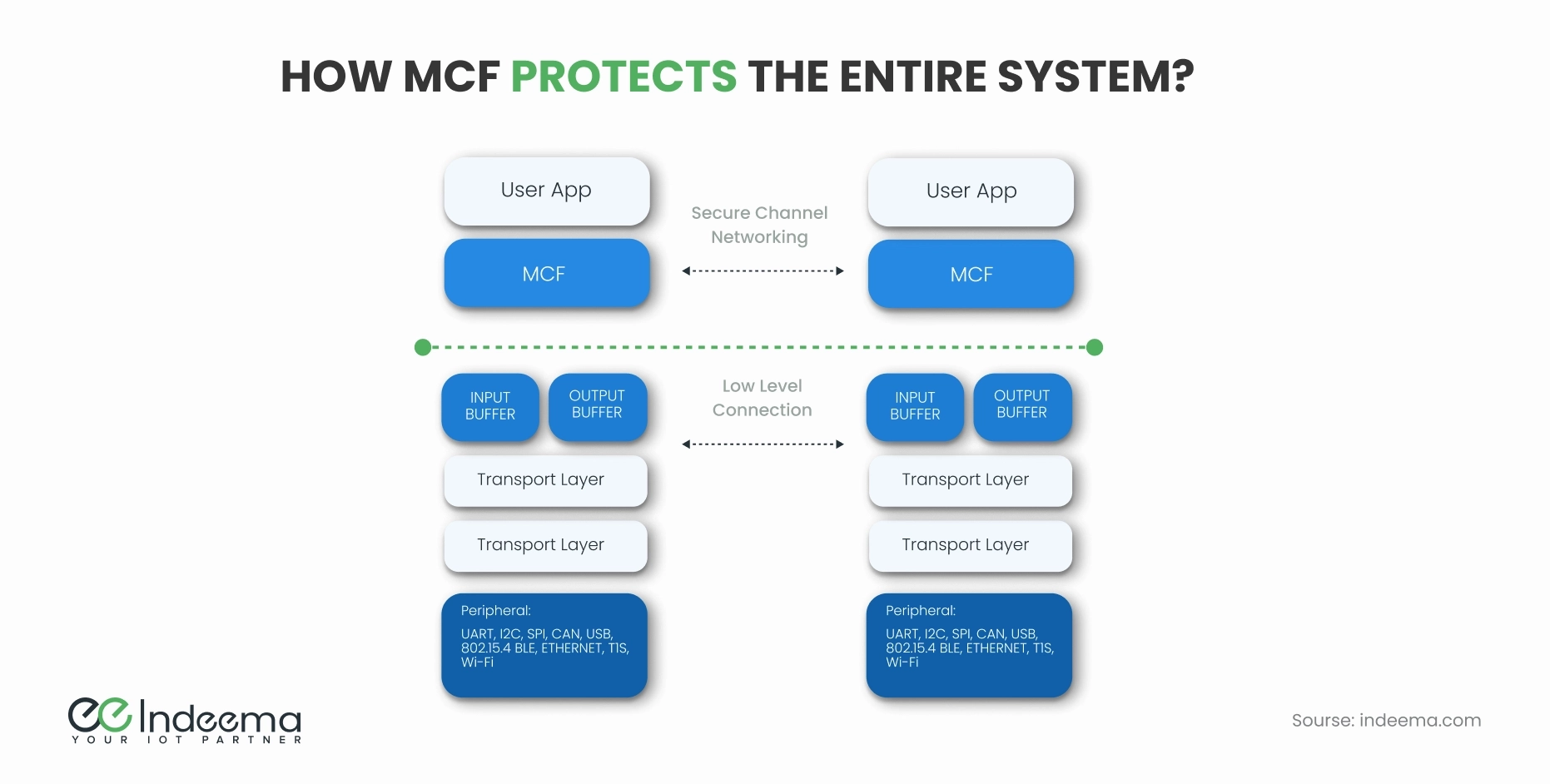
All interactions between IoT devices occur in this secure application layer. The data is encrypted end-to-end, which means a hacker will not be able to decipher it. MCF relies on lightweight messaging protocols and can be used even with limited bandwidth resources.
What sets MCF apart from other IoT messaging security frameworks is:
- Versatility: Developed with healthcare organizations in mind, MCF is applicable to virtually every type of IoT network. It works with any architecture (MCU 8, 16, 32bit, MPU) and peripheral (UART, SPI, CAN, T1S, Ethernet, Wi-Fi, 802.15.4, Bluetooth®, others).
- Lightweight protocols: MCF uses a standard MQTT broker.
- Legislative compliance: MCF simplifies compliance with NIS2, ETSI EN 303 645, and ISA/IEC 62443.
- Low memory usage: MCF only requires between 20 and 30 kB flash.
- Cloud support: The MCF application layer is located in the cloud. This is where all communication between IoT devices occurs, staying safe from attacks on the customer’s servers.
These features make MCF worth considering by everyone who wants to keep their and their customers’ data secure, whether it’s exchanged between IoT devices or an IoT device and a computer.
4. Protect your IoT device communication with MCF
You no longer have to choose between IoT connectivity and security or between built-in authentication and lightweight messaging protocols. Present-day security frameworks use multiple layers, combining authentication and encryption for optimal performance.
One of the most advanced frameworks is MCF, a proprietary technology patented by Microchip. It integrates seamlessly with virtually any existing security system, augmenting it with an innovative application layer and end-to-end encryption. Indeema Software partners with Microchip as the co-developer and an authorized distributor of MFC.
Would you like to learn more about MCF and how it can protect your data? Reach out, and we will gladly answer any of your questions.

_1721725124562.webp)
