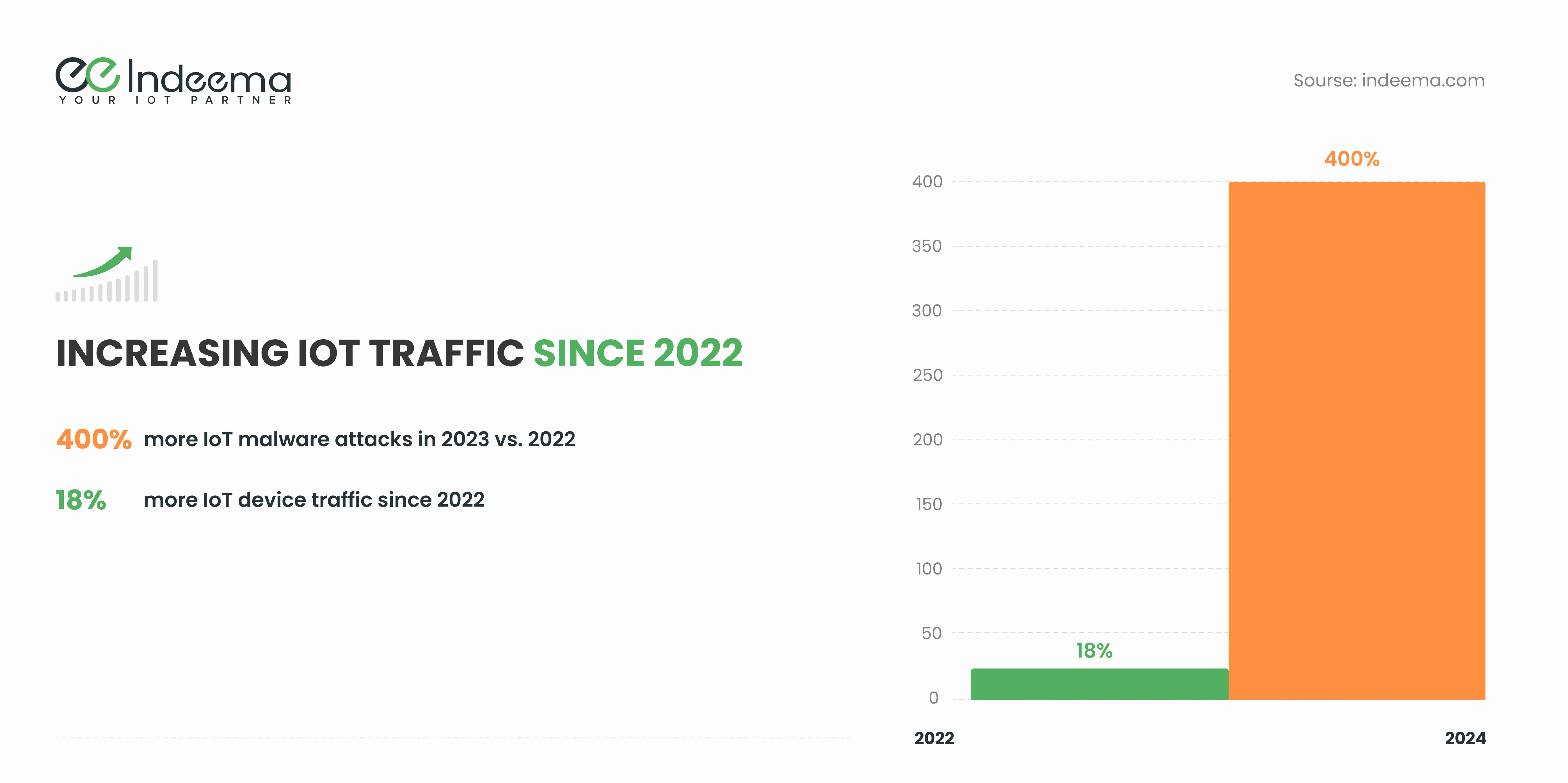
We know IoT data encryption best practices, right? Regularly update and patch devices, use strong encryption methods, implement robust authentication and authorization mechanisms, monitor network traffic for potential breaches, and so on. But, it turns out, this isn’t quite enough to ensure IoT security. IoT traffic has increased by 18% since 2022, and accordingly, malware attacks on IoT devices have risen 400%.
As a leading provider of embedded control solutions, Microchip Technology invests resources in solving this issue. And they have developed a solution: Microchip Connectivity Framework (MCF), the industry’s first application-layer stack that provides support for embedded IoT devices, PCs, and mobile applications, with optional hardware USB keys for maximum security.
We know you must have loads of questions about MCF. And since Indeema is Microchip’s official partner in integrating MCF, we’ll answer the most popular in this article:
- What problems does MCF solve?
- What industries and companies is MCF intended for?
- What is the technical core of MCF?
- What are MCF’s features and functions?
- How does MCF protect IoT devices?
- What are the benefits of adopting MCF?
- How do you implement MCF?
- Does MCF help with regulatory compliance?
Keep reading to discover insights about MCF, and you’ll see why it’s a significant advancement in IoT connectivity security.
1.What is Microchip Connectivity Framework (MCF)?
MCF is a handy set of software libraries and tools designed to make communication between embedded peripherals on a shared network a breeze. It operates at the application layer, above the existing low-level communication channels, which allows nodes to communicate via an on-premises server or through a cloud server. Plus, the framework lets any peripheral securely exchange information on the same network without the local server vendor or cloud service provider seeing the message content.
1.1 Key benefits of MCF adoption
The Microchip Connectivity Framework provides encrypted node-to-node communication through transparent and scalable shared cloud instances, dedicated cloud instances, or on-premises instances. This comes with a set of benefits:
- Protocol abstraction. MCF abstracts away whatever protocol is used for low-level communication and provides one common protocol for every device and node.
- Cloud agnostic. MCF makes you less dependent on cloud providers and allows you to easily transfer your MCF instance from or to other providers.
- Data transparency. Whether using cloud or on-premises infrastructure, the protocol ensures that vendors cannot see user data.
- User-controlled connections. Connections with devices are managed by the end customer using PKI.
- Strict data ownership. The framework ensures strict control of data ownership, preventing misuse or unauthorized access.
- Hardware encryption keys. End-to-end encryption can be implemented on both ends using custom USB keys provided by Microchip or Indeema.
- High portability. MCF is applicable to a wide range of architectures, including 8-, 16-, and 32-bit MCUs and MPUs.
- Various underlying communication channels. MCF works with UART, SPI, I2C, USB, CAN, T1S, Ethernet, Wi-Fi, 802.15.4, Bluetooth, and more.
- Security compliance. MCF adheres to rigorous security standards, implementing ECDSA (FIPS186-3 Elliptic Curve Digital Signature), ECDH (FIPS SP800-56A Elliptic Curve Diffie-Hellman), and HKDF (FIPS SP800-56C Key Derivation) for robust security.
- Flexible networking. MCF supports various topologies, including point-to-point, star, and mesh.
- Cloud support. Seamlessly integrates with standard MQTT brokers and includes a small application to extend networking capabilities through the cloud.
- Usability. Built-in functionality for session forming, routing, redundancy, and cloud connectivity makes MCF accessible to developers of all skill levels.
1.2 The building blocks of MCF
The MCF network is set up in clusters, each including one or more nodes and a gateway. Essentially, every node has to join or become a gateway to form a cluster. Within each cluster, the gateway keeps and shares a list of all the participating nodes. The communication between nodes is secured end-to-end.
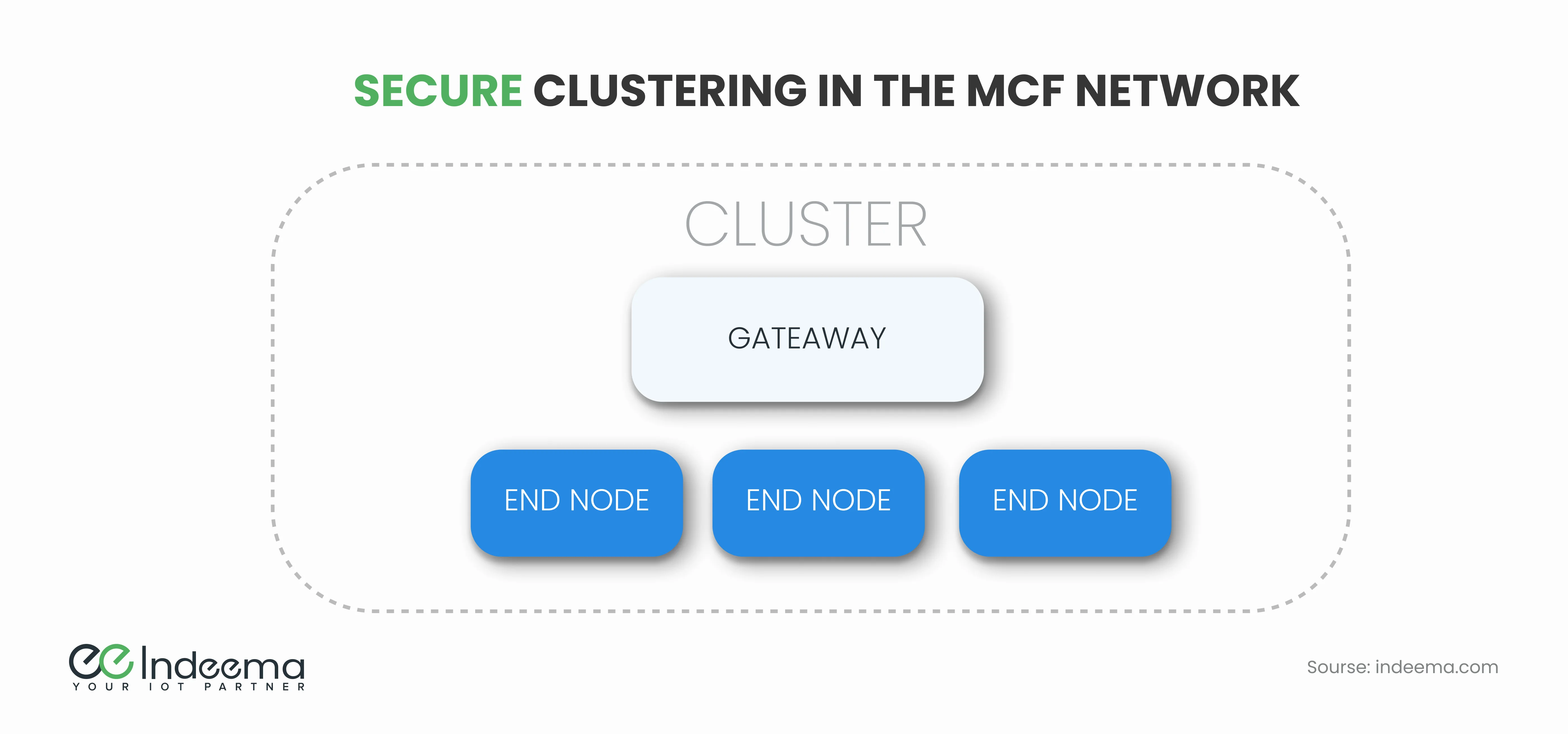
MCF just needs access to an input and output buffer, which are managed by the underlying drivers and stacks. In this way, the framework integrates with existing infrastructure like UART, CAN, Ethernet, Bluetooth, etc.
For secure sessions, each node is identified through a chain of certificates that verify authenticity. This chain includes certificate authority (CA), Server, Intermediate, and Device thumbprints, with the total size of the credentials being 600 bytes. Intermediate and Device certificates can be stored in Flash or a Secure Element for embedded devices, while Server and CA are stored in Flash.
1.3 What’s going on in the device and the cloud to make MCF work?
Device provisioning is entirely the customer's responsibility. While an IoT service provider can configure and maintain the cloud extension, the customer can also manage this task. The cloud remains transparent, ensuring that data privacy is maintained—there is no way for the provider to access the content of messages transmitted through the cloud.
1.4 MCF system requirements
- Minimal bandwidth needed: The messaging system is incredibly lightweight.
- Low memory requirements: Uses only 20kB to 30kB of Flash memory on the device.
- Broad MCU compatibility: Suitable for any MCU architecture, including 8, 16, 32-bit, and MPU.
- Protocol versatility: Operates over UART, SPI, CAN, T1S, Ethernet, Wi-Fi, 802.15.4, Bluetooth, and more.
- Routing capability: Supports point-to-point, star, and mesh configurations.
- Cloud extension: Runs a standard MQTT broker instance with a small application to facilitate cloud operation.
2. Practical aspects of using MCF
Understanding the practical aspects of MCF will help you effectively deploy and manage the framework in your IoT ecosystem, ensuring robust security, seamless communication, and flexible infrastructure support.
2.1 MCF node identification
The MCF device certificate includes a subject serial number (9 bytes), an issuer serial number (9 bytes), a public key (64 bytes), an expiration date (4 bytes), and a signature (64 bytes), totaling 150 bytes for the device thumbprint.
2.2 MCF provisioning and certificates
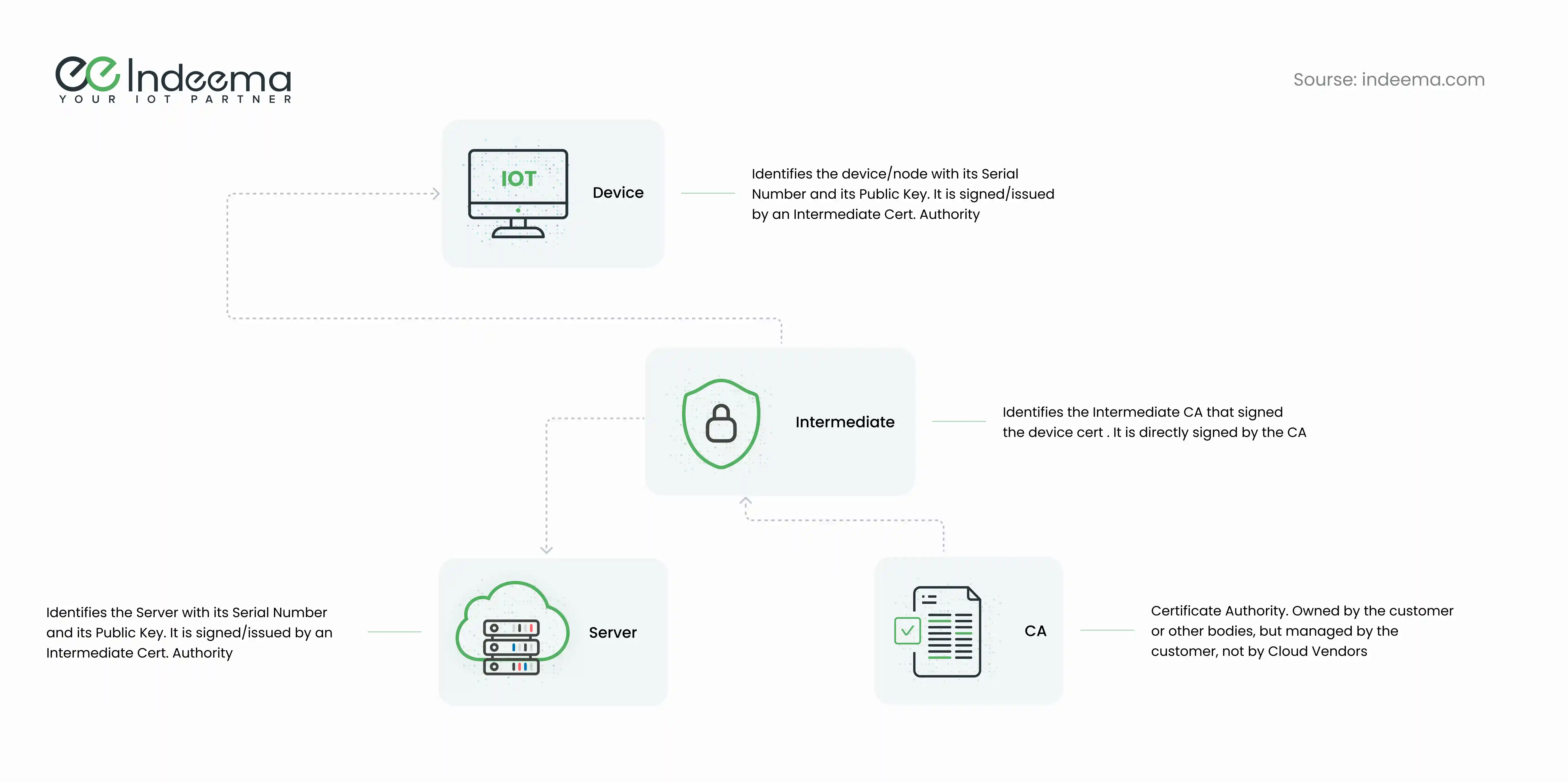
Each device certificate identifies the device or node with its serial number and public key and is signed by an intermediate certificate authority (CA). This intermediate CA is then signed by the CA. The server certificate identifies the server with its serial number and public key, and it's also signed by an intermediate certificate authority. The certificate authority is owned and managed by the customer, not by cloud vendors.
2.3 Using secure elements ICs
The most secure method involves Microchip creating an intermediate (private + public) key pair, which is then signed by the customer's CA. Microchip also ensures secure elements generate their private key and extract the public key to create a device thumbprint signed by the Microchip intermediate.
3. From Healthcare to Manufacturing: Industries Where Device Security Matters Most
Keyfactor recently ran a survey of 1,200 IoT and connected product professionals from North America, EMEA, and APAC working in manufacturing, IT, telecoms, energy, real estate, financial services, and other sectors. The findings revealed that just 43% of these respondents feel they are fully protected against IoT threats. However, 56% admitted that their organizations do not have adequate awareness or the essential expertise to defend against IoT attacks effectively.
Well, thanks to Indeema’s MCF implementation services, companies from various sectors can adopt the technology locally or through a cloud-based solution. Speaking of business sectors, those that might find MCF the most useful include:
- Embedded systems. If you design and build IoT devices, smart appliances, industrial controllers, or sensors, MCF can help make sure your devices communicate smoothly.
- Technology startups. For startups creating new IoT or connected device solutions, MCF can speed up your development process and ensure your products have strong communication capabilities.
- Enterprise IT. Big companies that use various connected devices for facility management, asset tracking, or process automation can use MCF to improve connectivity and security.
- Consumer electronics. Companies making smart home devices, wearables, or other consumer IoT products can add MCF to give their customers better connectivity features.
- Industrial automation and control systems. Businesses in this sector can use MCF for secure communication between industrial equipment, boosting efficiency and data collection.
- Healthcare technology. If you're developing healthcare devices and solutions, MCF ensures secure and reliable data exchange for medical devices and telehealth apps.
- Smart cities and infrastructure. For those working on smart city projects or infrastructure solutions, MCF enables efficient communication across different components of the smart city ecosystem.
- Automotive and transportation. Companies in this field can use MCF to enhance connectivity in connected vehicles and transportation systems.
- Military. Firms in the military sector can leverage MCF to secure communication between equipment.
You can also read our overview of the emerging frameworks designed to secure different types of IoT networks in healthcare, cloud services, and smart homes.
In addition, MCF can help companies comply with regulations and standards like NIS 2, ETSI EN 303 645, and ISA/IEC 62443. This is extremely important since 98% of respondents from Keyfactor’s survey claimed that regulations influence their development of IoT and connected products.
4. MCF: A Paradigm Shift in IoT Security
Microchip Connectivity Framework is a game changer that provides universal secure IoT connectivity at the application layer, ensuring end-to-end encryption and strict data ownership. It is highly portable and compatible with various MCU architectures and communication channels. Plus, being cloud agnostic, MCF works with any provider or on private servers.
MCF is designed to be user-friendly, making it ideal for data encryption in healthcare, smart homes, and vehicles. To get started, just reach out to Indeema, an official Microchip partner for MCF configuration. With our support, you'll enjoy a secure and transparent protocol while keeping full control over device provisioning.

_1724052646015.webp)
