Introduction
Without the cloud, no IoT project in the modern era can run. No, Really!
The main advantages of Internet of Things (IoT) solutions become apparent when processing data from numerous sensors or when keeping track of something for a long time. Data must be gathered, accumulated, and processed in one place. If the system is close to itself (production, agro-industry), you can use a local server for these tasks, otherwise, you can use a remote server. A server costs money to support and upgrade, and it isn't always fully involved.
For small solutions or startups whose market volume is not precisely known, such costs are completely unnecessary. However, even for global solutions, is frequently not financially advantageous to invest in efficient servers. Learn more about Cloud Platform for IoT.
1. Layers of Cloud Computing
It is possible to conditionally divide all cloud computing services into three layers, each of which utilizes a different model for offering cloud computing services to the user. Let's examine each layer, beginning with the bottom of the so-called cloud pyramid, which is the layer in which the service provider is most minimally involved.
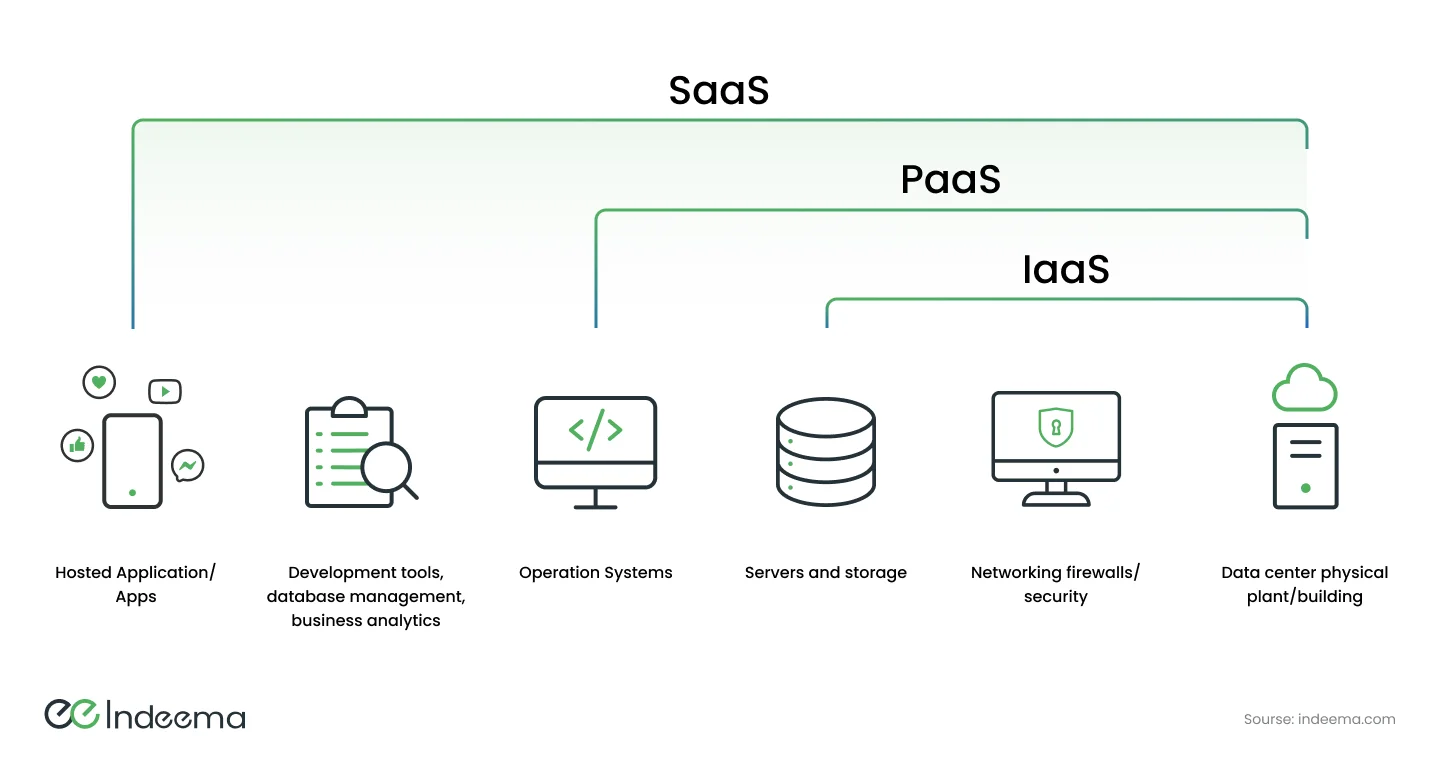
1.1 IaaS (Infrastructure as a Service)
This type of cloud model involves the allocation of certain computing and communication resources, which the user is free to utilize however he sees fit. The basis of IaaS is virtualization technology. The virtual machine orchestrator is hidden from the client but allows the provider to allocate as many resources (CPU time, disk space, network bandwidth) to the user as is needed right now, of course, within the limits of certain tariff plans.
Unlike hosting, where the client also receives certain resources for a subscription fee, IaaS is more flexible, allows you to use any custom software, and, in most cases, dynamically manage allocated resources during peak loads or downtime.
Examples of IaaS are large cloud service providers (AWS IaaS, Google Compute Engine, Azure Virtual Machines, DigitalOcean). You can also deploy the infrastructure on your own server using open-source software and manage resources using a virtual machine orchestrator. The most well-known project for building infrastructure from virtual servers is OpenStack.
1.2 PaaS (Platform as a service)
The next cloud service provisioning model involves supplying the user with system software and an information platform in addition to allocated resources. The user receives a ready-made operating system configured for the task, a database management system, and development and testing tools in the cloud. Unlike the IaaS model, the developer does not need to think about deployment and configuration. The development and testing of the project's unique attributes and business logic are the only things the developers pay any attention to in this case.
We have already talked about examples of PaaS. They are Google Cloud IOT, Amazon AWS IOT, and many others. But note that the payment of the platform may depend not only on the resources the developed system uses but also on the set of functionalities.
1.3 SaaS (Software as а Service)
The last model, SaaS, is at the top of the cloud services pyramid. In this case, cloud-deployed software adapted to solve a specific task is provided by subscription. We are interested in the application specifically for the Internet of Things because of the various types of tasks SaaS can solve. In this industry, cloud software may be useful in the following cases:
⚈ software for connecting devices can be adapted to a necessary manufacturer;
⚈ services for storage and processing of data, including with the help of artificial intelligence;
⚈ software for interacting with the client and displaying statistics;
⚈ specialized cloud IDEs for configuration, development and testing.
On the market, there are actually a lot of SaaS examples. According to this model, cloud service providers can include both the major market players (Google Cloud IoT Core, Microsoft Azure IoT Hub, AWS IoT Core, IBM Watson IoT, Oracle IoT) and hardware platform suppliers who offer specialized software for their products that has already been tested and set up.
An example of the latter is Avnet. In addition to offering SaaS services, it is a large distributor of electronic components. Indeema recently entered into a strategic partnership with Avnet, and as a result of our collaboration, we are better able to meet the needs of our clients and offer even more complex IoT services.
2. Which model will help to meet your IoT goals?
The use of cloud models like IaaS, Saas, and PaaS in projects frees enterprises from the need to support data centers and complex client and network infrastructures, and also allows them to reduce the associated capital and operational costs. But the choice of one or another model of receiving cloud services is critical for a successful decision. The hardware that will be used in the project, the innovativeness and complexity of the solution, the business model of the project, and others influence this choice. Therefore, let's consider several examples that can help you understand which model is right for you.
Explore Our Success Stories.
2.1 Is SaaS Right for Your Business Needs?
Let's say you have a great idea for a startup, and right now is a good time to enter the market to win over your users. When we talked about MVP, we emphasized that oftentimes, time to market can play a big role. Designing, debugging, and testing all the components required for a working IoT product is time-consuming even with the best team. The answer is to use SaaS. Ready-made software services may not cover all needs, but they will allow your product to quickly enter the market.
2.2 When to Choose PaaS Cloud Model?
If the main feature of your solution is unique data processing or business logic, and standard software can be used for all other parts of the project, the PaaS model will be the best choice. In this case, you will have enough options for customization, and at the same time, you don't need to do everything from scratch. An example would be the specific processing of data from video surveillance cameras when you use a ready-made hardware platform, data transmission, and storage services, but focus on your unique video processing offer.
2.3 When Choosing IaaS Makes More Sense
Use the IaaS model if your solution's software component runs locally but needs to be transferred to the cloud with little modification, or if it makes use of specialized software. In this case, the virtual machine completely replicates the required environment. And you can have as many of these virtual machines as you need in place of physical ones.
If it is planned to build a closed system that will be accessed only from the middle, for example, the automation of production, a warehouse, a farm, or a cyber factory, it may be worth limiting the local server or deploying a private cloud on it. However, if you plan to use global open services, you should also look towards the IaaS model. It must be said that the robotic factories that chose ROS, which we wrote about earlier, took IaaS for the deployment of remote management containers.
In general, the IaaS model is the most flexible and multifunctional but requires more capital investment and development time, so it is suitable for either large or specific, unique systems. Another great advantage of IaaS is the possibility of a simple migration to another provider because your solution does not depend on the provider's services. In contrast, the SaaS model provides the client with a set of ready-made but limited solutions.
The service provider will require additional funds for any additional functionality. However, the SaaS model provides a solution in the here and now, which is very necessary and sometimes cheaper. The PaaS model is a logical evolution of SaaS for customers who are uncomfortable with limitations but don't have the ability to build everything themselves. This model is suitable for most IoT solutions.
3. Security Issues in IoT and Cloud Computing Service Models
Unfortunately, every technology has flaws. The biggest issue with both cloud infrastructure services and the Internet of Things is security. The reason here is the same: a large number of entry points and nodes, as well as the complexity of the system as a whole. Only the local system itself, with no external exit, can be truly protected. However, because we operate open systems on a global network, additional forms of protection are needed. Authentication, authorization, encryption, and access rights are the cornerstones of information protection. Let's see how it works.
Depending on the cloud service delivery model, the developer, the user, and the provider each have a portion of the responsibility for security.
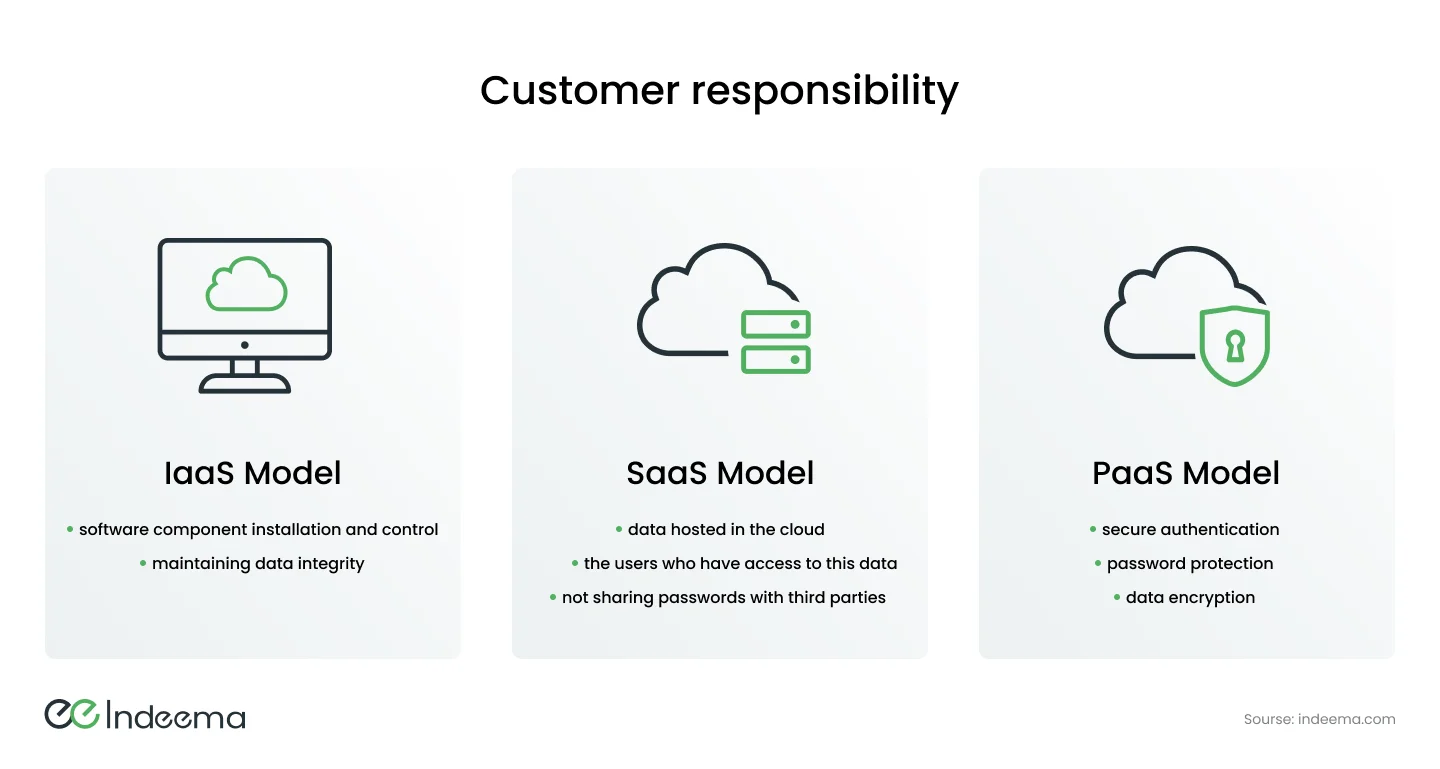
When utilizing the IaaS model, the service provider is only required to offer virtual machine isolation. Virtual machine data should not be accessed outside of it, virtual machines should not exchange data without authentication, etc. The customer is in charge of all other security duties. All software components must be installed, controlled, and used by the client on their own, along with maintaining data integrity.
In the SaaS model, on the contrary, almost all responsibility for security rests with the cloud service provider. The customer is only responsible for the data hosted in the cloud and the users who have access to this data, i.e., not to share their passwords with third parties. The provider is responsible for data encryption, saving of passwords on the cloud side, and access control.
The most difficult situation is in the case of the PaaS model since both the provider and the client are responsible for security. Most resources from the provider are allocated in the form of Docker containers, or microservices that interact with each other. A frequent fault of providers is improper allocation of permissions for interaction between containers. Sometimes it leads to instances of either task failures or insufficient protection.
Secure authentication, password protection, and data encryption should be the customer's concerns. To identify the user, it is better to use several communication channels at once for greater protection or to use hardware biometric sensors in the user terminal, for example, through a client application.
Despite the challenges of ensuring security in the cloud, it can generally be said that this issue has been resolved in the majority of instances. Most security problems are related to the human factor. Yet, it is important to note when selecting cloud computing service models which aspects of the overall infrastructure's security you agree to offer yourself and which parts can be trusted to the provider.
Let Our Client Success Stories Inspire You.
Conclusion
Cloud services are a modern requirement in IoT solutions. Other approaches to processing Internet of Things data are almost unthinkable. However, each IoT solution is unique and necessitates the most technological flexibility. As a result, various models for providing cloud capacity have evolved. Today, we attempted to determine which model would be most appropriate for your company. We hope you find this information useful.
