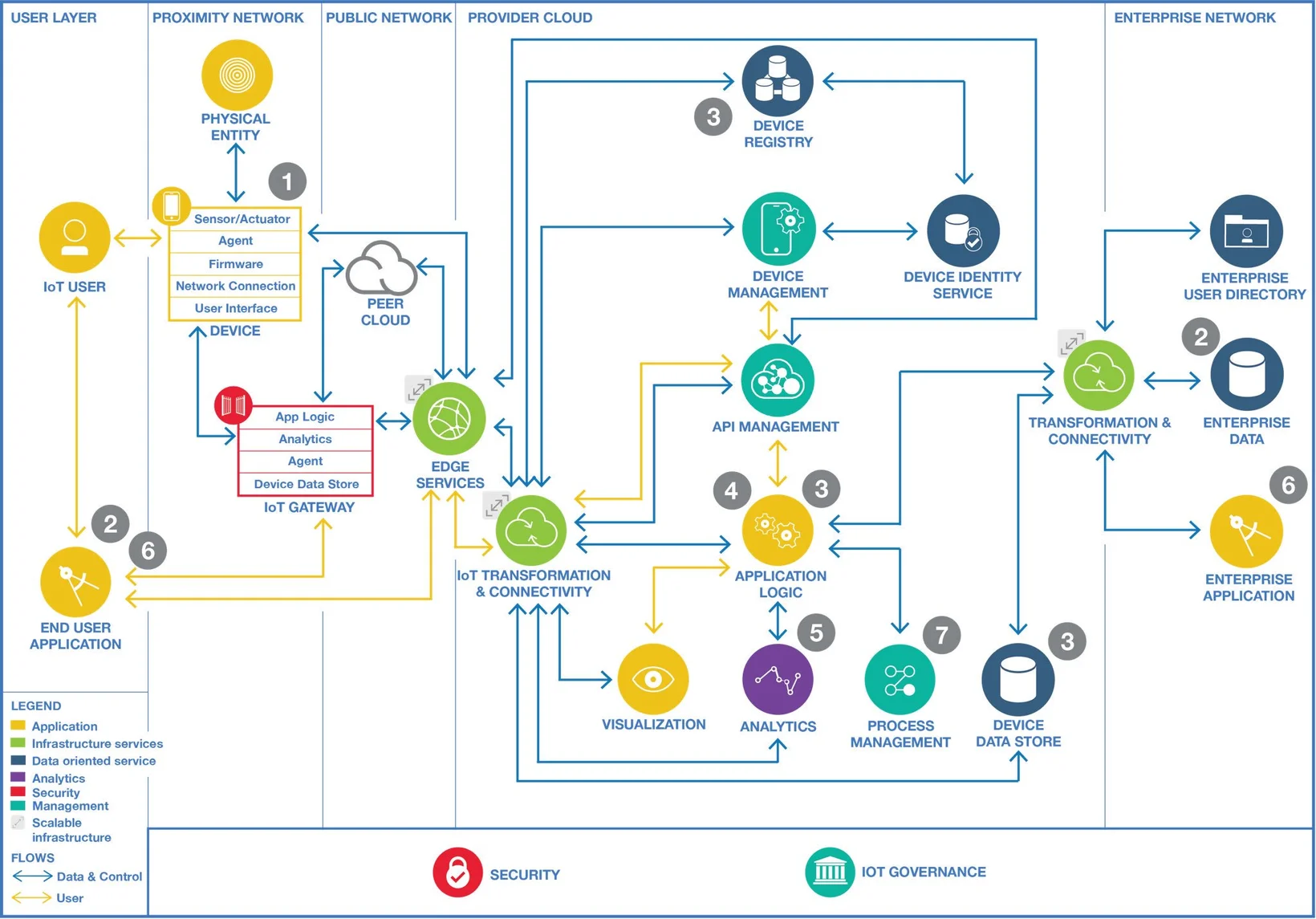
Introduction
Over the past few decades, computer systems have gone from clunky and slow to sleek and efficient.
And now, a new class of pint-sized powerhouses has emerged: small, affordable computers that come in single-board format. These tiny network devices pack a huge computing punch, and they're often situated right alongside the source of information - think Internet of Things devices, for instance. So it's no surprise that when we delve into the architecture of IoT systems (check out our article on IoT platforms), edge computing is a critical piece of the puzzle.
1. How IoT is Changing Computational Approaches
The explosive growth and increasing computing power of IoT devices have resulted in unprecedented volumes of data. And data volumes will continue to grow as 5G networks increase the number of connected mobile devices.
However, IoT devices themselves have limited processing capabilities, which makes them unsuitable for computation-intensive tasks. Therefore, IoT systems usually adhere to a cloud-centric architecture. But as data grows, computational approaches are changing.
Consider the basic paradigms of computation, depending on the requirements of the application:
1.1 Cloud Computing
This is a classic approach, using a centralized computing infrastructure that provides seamless access to powerful cloud servers. These servers can quickly process large volumes of data received from remote IoT devices and send the results back or to the client. However, latency-sensitive systems that operate in real-time cannot afford the long delays caused by data transmission over the WAN. Continuous transmission of bulk raw data over unreliable wireless channels can also be inefficient and insecure. The advantage of cloud computing is virtually unlimited computing power, which can be allocated depending on the task.

1.2 Cloudlet
Cloudlet is another form of hybrid, namely the middle section in the "mobile device - cloudlet - cloud" system for tasks that need to reduce delays, but require large cloud computing resources. In this case, part of the calculations most sensitive to delays are performed on the local (within the local network) computer center.

1.3 Edge Computing
Here, in contrast, all processing is decentralized, all the capabilities of cloud computing are provided directly near the IoT devices, i.e., at the edge of the network. An important type of such peripheral computing is mobile ad hoc cloud (MEC), which provides cloud computing capabilities at the border of the cellular network. Computing and data storage services, in the case of MEC, can be provided by mobile operator base stations.

1.4 Fog Computing
One variant of the hybrid between cloud and edge is fog technology, which uses local fog nodes (i.e., local area network devices such as a router or switch) available within a limited geographic area to provide computing services. Fog computing is considered to be the technology that is best suited for the Internet of Things. However, the disadvantage is the computing resource limitation of fog, especially during heavy network load.

It must be said that now the main method of processing the big data obtained by the Internet of Things is artificial intelligence. For a long time, complex AI calculations, especially in the case of ultra-deep neural networks, could only be performed in cloud data centers.
However, when it became clear that network delays were becoming uncomfortable for users, and sometimes unacceptable for the system at all, hardware vendors began producing low-cost, low-power computing systems optimized for large matrix mathematica. These computing devices become the basis of purely edge IoT computing and hybrid approaches such as the cloudlet.
2. What is Edge Computing?
Edge computing is one of the paradigms of distributed computing, according to it, data is stored and processed within a "first mile" from the source of this data. Some tasks take too long and are too expensive to transmit data over communication channels, and it may even be pointless.
 Despite the increase in bandwidth of communication channels, the growth of data volumes is faster and will continue to overload intermediate servers and data centers. Typical examples of systems where it is necessary to perform calculations on the edge are:
Despite the increase in bandwidth of communication channels, the growth of data volumes is faster and will continue to overload intermediate servers and data centers. Typical examples of systems where it is necessary to perform calculations on the edge are:
- CCTV cameras video analysis systems -- the cameras generate too much data, which is impractical to transfer to remote servers or the cloud for processing and storage;
- Control of robots and cybernetic devices, including autopilot in a smart car – for such systems critical is the speed of reaction to changes in the environment, decisions must be made in real-time, even small delays in data transmission can lead to the inoperability of such systems.
3. Edge Computing Benefits
The following benefits of edge computing in IoT for different information systems can be identified:
3.1 Low Latency
By processing data at the edge, data travel is reduced or even eliminated. This allows more complex data processing for systems that require an immediate response and significantly increases the use of such systems.
3.2 Cost Reduction
One of the biggest benefits of edge computing is the potential cost reduction it brings to IoT systems. By moving data processing to the edge - that is, closer to where the data is generated - less data needs to be sent to data centers and the cloud for further computation. This means that the amount of data that the cloud has to work with is reduced, which in turn reduces the overall cost of operating the system.
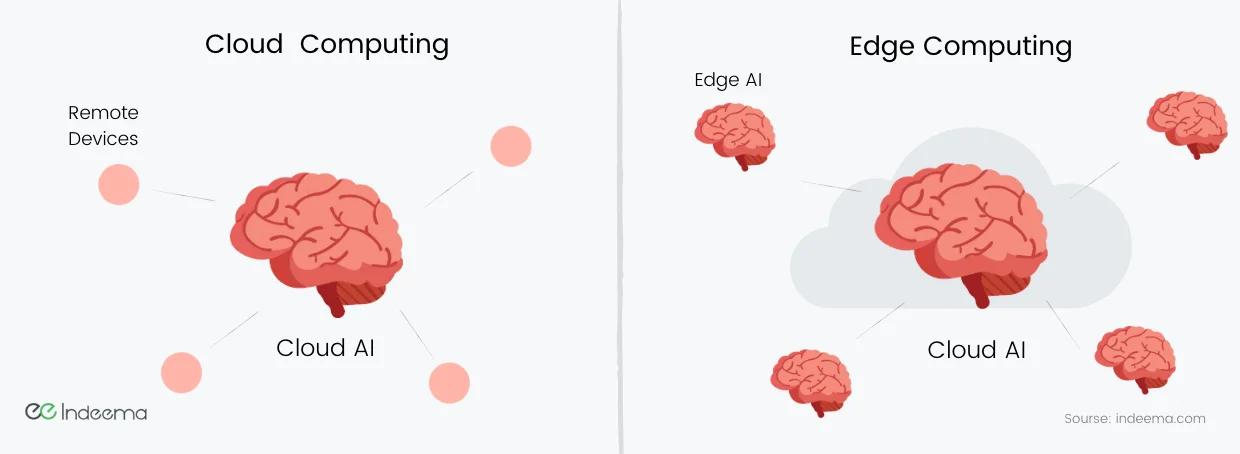
3.3 Edge AI
AI is increasingly used for data processing. In the classical approach, the data is transferred to the cloud service, where it is processed using AI models, and the user receives certain conclusions. The barrier is data speed limits, especially for tasks that require an immediate response.
The solution was to reduce the size of the data sets (reduce image sizes, skip frames in a video, and reduce sample rates in audio), but this brings down the accuracy of AI models, so impairs the reliability of the results.
Moving AI models to the edge will let us avoid such problems, as they will work with complete data, increasing response speed and accuracy. Good examples of such changes are face authentication and speech recognition directly on the user's smartphone when the data does not go out of the device. Many manufacturers already offer equipment for edge computing, focused on artificial intelligence.
3.4 Data Sovereignty
Another key benefit of edge computing is data sovereignty. Data sovereignty refers to the concept that data is subject to the laws and governance of the country or region where it is stored or processed. With edge computing, data can be stored and processed locally, which means that businesses can have greater control over their data and ensure that it is compliant with local regulations.
If edge devices are located within a company's local network, there is no need to worry about an additional level of protection. The existing infrastructure and firewall can be used to protect the data and ensure its privacy and security. This means that businesses can be confident that their data is secure and that they are complying with relevant data protection regulations.
4. The Intersection of IoT and Edge: A Closer Look at Their Similarities
IoT and edge computing are state-of-the-art technologies that are revolutionizing practically every aspect of life and business. Let's examine three parallels between the two:
4.1 Emerging Technologies
IoT and edge are cutting-edge technologies that have a significant impact on corporate operations in all industries. In manufacturing, for example, IoT sensors can be used to monitor the performance of factory equipment, providing real-time data on things like temperature, pressure, and vibration. This data can be processed at the edge, allowing for immediate analysis and the identification of potential issues before they become major problems. Similarly, in healthcare, IoT devices can be used to monitor patients remotely, providing doctors and nurses with real-time data on things like heart rate, blood pressure, and oxygen levels.
4.2 Data-Founded
IoT and edge are based on data collection and analytics, although the specifics of how they accomplish this can differ.
IoT devices are designed to collect data from sensors and other sources, and then transmit that data to the cloud for analysis and storage. In contrast, edge computing involves processing data on devices located at the edge of the network, such as routers, switches, and gateways.
4.3 Sensors
IoT and edge devices rely on sensors to collect data from the physical world. These sensors can come in a variety of forms, such as temperature sensors, motion sensors, and pressure sensors, to name a few. Once the sensors have collected data, IoT and edge devices can use that data for additional processing. This could include performing calculations, running machine learning algorithms, or making decisions based on the collected data.
For example, in a smart home system, temperature sensors can be used to collect data on the temperature in each room of the house. This data can then be processed by an edge device, such as a smart thermostat, to adjust the temperature based on user preferences or pre-set schedules.
5. Edge Computing and IoT: Ensuring Security
Internet of Things systems solve many problems in production and everyday life, and increasingly affect our lives. But with the growing number of IoT devices, there are new issues, and challenges for developers. The low computing performance of these devices not only does not allow them to process the data received, as we mentioned above, but also has an insufficient level of security.
When more and more devices are connected to the system, the security difficulty comes first. By gaining access to devices, attackers can get confidential information about people's health and everyday lives, and they can also be used, for example, to carry out DDoS attacks.
The way is to ensure the security of information on the edge. Of course, the protection that can be obtained on local clouds and edge computing devices can be weaker than on centralized clouds, but the benefits are significant.
The following requirements must be met to ensure high-level protection and security for edge computing:
- 👉 Secure perimeter: It is essential to provide secure access to edge computing resources (and therefore the Internet of Things) through encrypted tunnels, firewalls, and access control. If the system is located within the same organization/building/household, the existing infrastructure and local network can be used for these issues.
- 👉 Securing applications: The applications that edge computing devices run need to be secured beyond the network layer.
- 👉 Early threat detection: Due to the decentralized architecture of edge computing in the IoT, it is crucial to dynamically identify potential threats and violations. This includes identifying IoT devices or nodes of the computer system that may not be trusted, or captured by an attacker.
- 👉 Patch cycles: To ensure a rapid response, all problems and vulnerabilities must be corrected as soon as possible. This requires a rapid update to close existing "holes."
- 👉 Managing vulnerabilities: There should be continuous monitoring to detect unknown vulnerabilities in the system and eliminate them promptly.
Various approaches are employed to ensure security, and one of them is the "zero trust" or "least access" policy. According to this policy, each device in the system is granted only the minimum access necessary for its smooth functioning. From this perspective, each IoT device has its own specific purpose and therefore can use a limited set of secure protocols. This way, even if one device is compromised, the system as a whole remains safe and the critical resources remain protected.
It is worth noting that based on the principles of "zero trust," the Secure Access Service Edge (SASE) strategy was introduced in 2019. It is expected that most companies will adopt this strategy in the near future, given its effectiveness in ensuring comprehensive security.
Physical protection of the devices is also important. Most manufacturers of edge computing hardware already incorporate special chips (hardware security modules) that provide a hardware root of trust, crypto-based ID, encryption for in-flight and at-rest data, and automated patching.
6. IoT and Edge Computing Use Cases
Any Internet of Things (IoT) solution that calls for low latency or local data storage can benefit greatly from edge computing.

Listed below are some intriguing use cases:
6.1 Using visual inference
A high-resolution camera equipped with an IoT edge computer can watch video streams and analyze the information gathered. Intruders in prohibited areas, people with excessive body temperatures, safety infractions, an anomaly on the production line, etc. can all be found with that device.
6.2 Condition-based remote monitoring
Using the edge and iot to monitor the system makes perfect sense in situations where a failure may be catastrophic (such as an oil or gas pipeline). Temperature, pressure, tension, and other conditions can be monitored by an IoT sensor, and the edge server can identify and react to a possible problem in milliseconds.
6.3 Autonomous vehicles
Real-time data collection and processing must be possible for an autonomous car to collect while on the road (traffic, pedestrians, street signs, stop lights, etc.). Since automatic cars are a zero-latency use case, Edge IoT is the only way to guarantee that a self-driving car can stop or turn quickly enough to avoid an accident.
6.4 Industrial IoT (IIoT)
IoT sensors can monitor the condition of industrial gear and spot problems like failures or abuse. An edge server can address issues in the interim before a potential catastrophe.
6.5 Smart cities
Another application for edge computing that has a lot of potential is smart cities. Massive IoT networks are used by smart cities to collect and process data in order to enhance communication, influence policy, and run public services more effectively. Real-time insights would be improved, and these crucial activities would be made more secure with a deeper analysis of all this data.
Conclusion
The convergence of IoT and edge computing has brought about a new era of innovation and efficiency. While the two technologies may have distinct differences, they work in tandem to deliver powerful and cost-effective solutions across industries.
As the world becomes increasingly connected, the need for secure and efficient data processing at the edge has become paramount. With the implementation of proper security measures and the integration of hardware root of trust, edge computing has become a safe and efficient solution for businesses looking to take advantage of IoT technologies.
Looking to the future, it is clear that edge computing will continue to grow in importance, with the majority of data processing set to occur outside the cloud and data centers by 2025.
In conclusion, the future of IoT and edge computing is bright, with both technologies set to play a significant role in shaping the digital landscape of tomorrow.


